It may be surprising to the reader that there exist simple ``perfect'' encryption methods, meaning that there is a mathematical proof that cryptanalysis is impossible. The term ``perfect'' in cryptography also means that after an opponent receives the ciphertext he has no more information than before receiving the ciphertext.
The simplest of these perfect methods is called the one-time pad. Later discussion explains why these perfect methods are not practical to use in modern communications. However, for the practical methods there is always the possibility that a clever researcher or even a clever hacker could break the method. Also cryptanalysts can break these other methods using brute-force exhaustive searches. The only issue is how long it takes to break them. With current strong cryptographic algorithms, the chances are that there are no short-cut ways to break the systems, and current cryptanalysis requires decades or millennia or longer to break the algorithms by exhaustive search. (The time to break depends on various factors including especially the length of the cryptographic key.) To summarize, with the practical methods there is no absolute guarantee of security, but experts expect them to remain unbroken. On the other hand, the One-Time Pad is completely unbreakable.
The One-Time Pad is just a simple variation on the Beale Cipher. It starts with a random sequence of letters for the standard text (which is the key in this case). Suppose for example one usesRQBOPS as the standard text, assuming these are 6 letters chosen completely at random, and suppose the message is the same. Then encryption uses the same method as with the Beale Cipher, except that the standard text or key is not a quotation from English, but is a random string of letters.
Standard text (random key): RQBOPSMessage: ATTACKEncrypted message: RJUORC
So, for example, the third column uses the letter B, representing a rotation of 1, to transform the plaintext letter T into the ciphertext letter U. The receiver must have the same random string of letters around for decryption: RQBOPS in this case. As the important part of this discussion, I want to show that this method is perfect as long as the random standard text letters are kept secret. Suppose the message is GIVEUP instead of ATTACK. If one had started with random letters LBYKXN as the standard text, instead of the letters RQBOPS, then the encryption would have taken the form:
Standard text (random key): LBYKXNMessage: GIVEUPEncrypted message: RJUORC
The encrypted message (ciphertext) is the same as before, even though the message is completely different. An opponent who intercepts the encrypted message but knows nothing about the random standard text gets no information about the original message, whether it might be ATTACK or GIVEUP or any other six-letter message. Given any message at all, one could construct a standard text so that the message is encrypted to yield the ciphertext RJUORC. An opponent intercepting the ciphertext has no way to favor one message over another. It is in this sense that the one-time pad is perfect.
In this century spies have often used one-time pads. The only requirement is text (the pad) of random letters to use for encryption or decryption. (In fact, even now I would not want to be found in a hostile country with a list of random-looking letters.) The party communicating with the spy must have exactly the same text of random letters. This method requires the secure exchange of pad characters: as many such characters as in the original message. In a sense the pad behaves like the encryption key, except that here the key must be as long as the message. But such a long key defeats a goal of cryptography: to reduce the secrecy of a long message to the secrecy of a short key. If storage and transmission costs keep dropping, the one-time pad might again become an attractive alternative.
Bibliography
http://www.cs.utsa.edu/~wagner/laws/pad.html
https://mice.cs.columbia.edu/getTechreport.php?techreportID=1460
http://en.wikipedia.org/wiki/One-time_pad
http://www-rohan.sdsu.edu/~gawron/crypto/lectures/vigenere.html
Start
Codigo
Funcionamiento :
The first thing to do is generate the list's book once you give it to hand to the other person as you will need to decrypt the message
Number of keys >> is the number of elements or sheets of notepad then we have 100 keys to use
Characters >> is the number of characters to count each key.
One time Pad
2.We will create a file called message.txt containing our secret message for example take the phrase Internet
3 Now follow encrypt the message takes key 1 determines the size of the message and then modifies the size of the message key in conclusion are the same size and the message encryption key when the message is deleted from the OTP key and then to start this line 2 which is the next key to use
4 Now we have to send the encrypted message to person B and person B should have the OTP generated to test what we will do is copy the key 1 are separated by the symbol | and encrypt any message after hitting the key must anteriorimente copied and paste to start and decrypt.
The person decifrara the message has the OTP with the key used to decrypt but every time a key is to be borara zeros eg encrypt it in several times
Manual :
Generate codes one time pad =>python otp.py -oCifrar =>python otp.py -eDecifrar =>python otp.py -dSe generan los siguientes archivos:mensaje.txt : contiene el mensajecipher.txt : mensaje encrypteddecipher.txt : mensaje decifradokey.txt : libreta(OTP)
Cipher vigenre :
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution.
The Vigenère (French pronunciation: [viʒnɛːʁ]) cipher has been reinvented many times. The method was originally described byGiovan Battista Bellaso in his 1553 book La cifra del. Sig. Giovan Battista Bellaso; however, the scheme was later misattributed to Blaise de Vigenère in the 19th century, and is now widely known as the "Vigenère cipher"
This cipher is well known because while it is easy to understand and implement, it often appears to beginners to be unbreakable; this earned it the description le chiffre indéchiffrable (French for 'the indecipherable cipher'). Consequently, many people have tried to implement encryption schemes that are essentially Vigenère ciphers, only to have them broken
Algebraic description
Vigenère can also be viewed algebraically. If the letters A–Z are taken to be the numbers 0–25, and addition is performed modulo 26, then Vigenère encryption 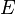 using the key
using the key  can be written,
can be written,
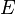 using the key
using the key  can be written,
can be written,
and decryption 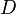 using the key
using the key  ,
,
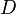 using the key
using the key  ,
, ,
,
whereas 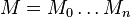 is the message,
is the message,  is the ciphertext and
is the ciphertext and  is the used key.
is the used key.
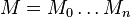 is the message,
is the message,  is the ciphertext and
is the ciphertext and  is the used key.
is the used key.
Thus using the previous example, to encrypt  with key letter
with key letter 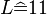 the calculation would result in
the calculation would result in  .
.
 with key letter
with key letter 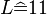 the calculation would result in
the calculation would result in  .
.
Therefore to decrypt 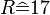 with key letter
with key letter  the calculation would result in
the calculation would result in 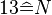 .
.
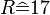 with key letter
with key letter  the calculation would result in
the calculation would result in 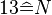 .
.




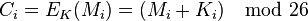


Bien; sería aún mejor teniendo comentarios en el código y si estuviera en inglés ;) Van los 5 pts.
ResponderEliminar