Las entradas fueron cambiadas al nuevo blog :
http://wordpress.rafaellopezgtz.com/
Information security and cryptography
martes, 30 de octubre de 2012
miércoles, 5 de septiembre de 2012
Diffie-Hellman Key Exchange
The Diffie-Hellman key agreement protocol (1976) was the first practical method for establishing a shared secret over an unsecured communication channel.
The point is to agree on a key that two parties can use for a symmetric encryption, in such a way that an eavesdropper cannot obtain the key.
Steps in the algorithm:
But it is not only sufficiently large values of the exponents that give security to this system. The choice of gyn also has a marked influence. The modulus n must be a prime number and, more important than this, (n-1) / 2 must also be a prime number. The base g, on the other hand, must be a primitive root modulo n in (more on the matter immediately below). Now, the most important of all is that n should be large, there is at least 512 bits
- Alice and Bob agree on a prime number p and a base g.
- Alice chooses a secret number x, and sends Bob (gxmod p)
- Bob chooses a secret number y, and sends Alice (gymod p)
- Alice computes ((gymod p)x mod p).
- Bob computes ((gx mod p)y mod p).
Example:
- Alicea nd Bob agree on p=23 and g=5.
- Alice chooses a=6 and sends 56 mod23=8
- Bob chooses b = 15 and sends 515 mod 23 = 19.
- Alice computes 196 mod 23 = 2.
- Bob computes 815 mod 23 = 2
Hack alice and Bob Manually
Hack used Program in python
---------
lunes, 27 de agosto de 2012
Statistical Analysis Randomness OTP
Statistical analysis was performed by one-time pad where it is determined if the generator is random or not
NIST test was used which included:
Spectral Test
-----
-----
Histogram
Changed the random generator
/dev/random and /dev/urandom are also available on Solaris, Mac OS X, NetBSD, Tru64 UNIX 5.1B, AIX 5.2, and HP-UX 11i v2. As with FreeBSD, AIX implements its own Yarrow-based design, however AIX uses considerably fewer entropy sources than the standard /dev/random implementation and stops refilling the pool when it thinks it contains enough entropy
Yarrow is a PRNG; it generates cryptographically secure pseudorandom numbers on a computer. It can also be used as a real random number generator, accepting random inputs from analog random sources. We wrote Yarrow because after analyzing existing PRNGs and breaking our share of them, we wanted to build something secure.
Source
Random generator was tested with independent evidence
References:
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
http://www.dia.fi.upm.es/~ajimenez/Docu_Simulacion/Transparencias/Cap1-GenNumAleat.pdf
http://www.scribd.com/doc/71375513/6/Analisis-de-Aleatoriedad-con-visualizacion-3-D
http://jair.lab.fi.uva.es/~pablfue/leng_simulacion/slides/0607/alea_t_0607.pdf
http://www.scribd.com/doc/50639457/16/Pruebas-de-aleatoriedad
http://www.scribd.com/doc/58547826/documentatie-licenta
http://www.fi.muni.cz/~xkrhovj/lectures/2005_PA168_Statistical_Testing_slides.pdf
http://www.doughellmann.com/PyMOTW/random/
http://gerhardt.ch/random.php
NIST test was used which included:
- Frequency Test: MonoBit
- Frequency Test: Block
- Runs Test
- Discrete Fourier Transform (Spectral Test)
Test Monobit
The focus of the test is the proportion of zeroes and ones for the entire sequence. The purpose of this test is to determine whether the number of ones and zeros in a sequence are approximately the same as would be expected for a truly random sequence. The test assesses the closeness of the fraction of ones to ?, that is, the number of ones and zeroes in a sequence should be about the same. All subsequent tests depend on the passing of this test; there is no evidence to indicate that the tested sequence is non-random.
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
Frequency Test: Block
The frequency (or frequency within a block) test is used to test the randomness of a sequence of zeroes and ones (Dataplot will covert a data set with exactly two distinct values to a sequence of zeroes and ones). The test is based on the proportion of zeroes and ones. Specifically, it tests the closeness of the proportion of ones to 0.5. The frequency within a block test is a refinement that tests the proportion of ones within M-value blocks
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
Run Test
The purpose of this test, as stated is to determine whether the number of runs of ones and zeroes of various lengths is as expected for a random sequence. A run is anuninterrupted sequence of identical bits. A run of length k consists of exactly k identical bits bounded before and after with a bit of the opposite value. Practically, this test determines if the oscillation between the runs of ones and zeroes in the sequence is too slow or too fast
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
Determine the max distance between adjacent hyper-planes.
http://www.cse.wustl.edu/~jain/cse567-08/ftp/k_27trg.pdf
We performed the following code in python for testing:
http://www.cse.wustl.edu/~jain/cse567-08/ftp/k_27trg.pdf
We performed the following code in python for testing:
-----
Histogram
We performed a program graph the frequency of each letter in this case each number from 0 to 25 numbers that are used for one time pad can be analyzed as frequency behaves.
Code:
Changed the random generator
/dev/random and /dev/urandom are also available on Solaris, Mac OS X, NetBSD, Tru64 UNIX 5.1B, AIX 5.2, and HP-UX 11i v2. As with FreeBSD, AIX implements its own Yarrow-based design, however AIX uses considerably fewer entropy sources than the standard /dev/random implementation and stops refilling the pool when it thinks it contains enough entropy
Random generator was tested with independent evidence
In another post where esplique each method in detail as is done
References:
http://csrc.nist.gov/publications/nistpubs/800-22-rev1a/SP800-22rev1a.pdf
http://www.dia.fi.upm.es/~ajimenez/Docu_Simulacion/Transparencias/Cap1-GenNumAleat.pdf
http://www.scribd.com/doc/71375513/6/Analisis-de-Aleatoriedad-con-visualizacion-3-D
http://jair.lab.fi.uva.es/~pablfue/leng_simulacion/slides/0607/alea_t_0607.pdf
http://www.scribd.com/doc/50639457/16/Pruebas-de-aleatoriedad
http://www.scribd.com/doc/58547826/documentatie-licenta
http://www.fi.muni.cz/~xkrhovj/lectures/2005_PA168_Statistical_Testing_slides.pdf
http://www.doughellmann.com/PyMOTW/random/
http://gerhardt.ch/random.php
miércoles, 22 de agosto de 2012
[HomeWork] One Time Pad
It may be surprising to the reader that there exist simple ``perfect'' encryption methods, meaning that there is a mathematical proof that cryptanalysis is impossible. The term ``perfect'' in cryptography also means that after an opponent receives the ciphertext he has no more information than before receiving the ciphertext.
The simplest of these perfect methods is called the one-time pad. Later discussion explains why these perfect methods are not practical to use in modern communications. However, for the practical methods there is always the possibility that a clever researcher or even a clever hacker could break the method. Also cryptanalysts can break these other methods using brute-force exhaustive searches. The only issue is how long it takes to break them. With current strong cryptographic algorithms, the chances are that there are no short-cut ways to break the systems, and current cryptanalysis requires decades or millennia or longer to break the algorithms by exhaustive search. (The time to break depends on various factors including especially the length of the cryptographic key.) To summarize, with the practical methods there is no absolute guarantee of security, but experts expect them to remain unbroken. On the other hand, the One-Time Pad is completely unbreakable.
The One-Time Pad is just a simple variation on the Beale Cipher. It starts with a random sequence of letters for the standard text (which is the key in this case). Suppose for example one usesRQBOPS as the standard text, assuming these are 6 letters chosen completely at random, and suppose the message is the same. Then encryption uses the same method as with the Beale Cipher, except that the standard text or key is not a quotation from English, but is a random string of letters.
Standard text (random key): RQBOPSMessage: ATTACKEncrypted message: RJUORC
So, for example, the third column uses the letter B, representing a rotation of 1, to transform the plaintext letter T into the ciphertext letter U. The receiver must have the same random string of letters around for decryption: RQBOPS in this case. As the important part of this discussion, I want to show that this method is perfect as long as the random standard text letters are kept secret. Suppose the message is GIVEUP instead of ATTACK. If one had started with random letters LBYKXN as the standard text, instead of the letters RQBOPS, then the encryption would have taken the form:
Standard text (random key): LBYKXNMessage: GIVEUPEncrypted message: RJUORC
The encrypted message (ciphertext) is the same as before, even though the message is completely different. An opponent who intercepts the encrypted message but knows nothing about the random standard text gets no information about the original message, whether it might be ATTACK or GIVEUP or any other six-letter message. Given any message at all, one could construct a standard text so that the message is encrypted to yield the ciphertext RJUORC. An opponent intercepting the ciphertext has no way to favor one message over another. It is in this sense that the one-time pad is perfect.
In this century spies have often used one-time pads. The only requirement is text (the pad) of random letters to use for encryption or decryption. (In fact, even now I would not want to be found in a hostile country with a list of random-looking letters.) The party communicating with the spy must have exactly the same text of random letters. This method requires the secure exchange of pad characters: as many such characters as in the original message. In a sense the pad behaves like the encryption key, except that here the key must be as long as the message. But such a long key defeats a goal of cryptography: to reduce the secrecy of a long message to the secrecy of a short key. If storage and transmission costs keep dropping, the one-time pad might again become an attractive alternative.
Bibliography
http://www.cs.utsa.edu/~wagner/laws/pad.html
https://mice.cs.columbia.edu/getTechreport.php?techreportID=1460
http://en.wikipedia.org/wiki/One-time_pad
http://www-rohan.sdsu.edu/~gawron/crypto/lectures/vigenere.html
Start
Codigo
Funcionamiento :
The first thing to do is generate the list's book once you give it to hand to the other person as you will need to decrypt the message
Number of keys >> is the number of elements or sheets of notepad then we have 100 keys to use
Characters >> is the number of characters to count each key.
One time Pad
2.We will create a file called message.txt containing our secret message for example take the phrase Internet
3 Now follow encrypt the message takes key 1 determines the size of the message and then modifies the size of the message key in conclusion are the same size and the message encryption key when the message is deleted from the OTP key and then to start this line 2 which is the next key to use
4 Now we have to send the encrypted message to person B and person B should have the OTP generated to test what we will do is copy the key 1 are separated by the symbol | and encrypt any message after hitting the key must anteriorimente copied and paste to start and decrypt.
The person decifrara the message has the OTP with the key used to decrypt but every time a key is to be borara zeros eg encrypt it in several times
Manual :
Generate codes one time pad =>python otp.py -oCifrar =>python otp.py -eDecifrar =>python otp.py -dSe generan los siguientes archivos:mensaje.txt : contiene el mensajecipher.txt : mensaje encrypteddecipher.txt : mensaje decifradokey.txt : libreta(OTP)
Cipher vigenre :
The Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution.
The Vigenère (French pronunciation: [viʒnɛːʁ]) cipher has been reinvented many times. The method was originally described byGiovan Battista Bellaso in his 1553 book La cifra del. Sig. Giovan Battista Bellaso; however, the scheme was later misattributed to Blaise de Vigenère in the 19th century, and is now widely known as the "Vigenère cipher"
This cipher is well known because while it is easy to understand and implement, it often appears to beginners to be unbreakable; this earned it the description le chiffre indéchiffrable (French for 'the indecipherable cipher'). Consequently, many people have tried to implement encryption schemes that are essentially Vigenère ciphers, only to have them broken
Algebraic description
Vigenère can also be viewed algebraically. If the letters A–Z are taken to be the numbers 0–25, and addition is performed modulo 26, then Vigenère encryption 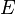 using the key
using the key  can be written,
can be written,
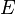 using the key
using the key  can be written,
can be written,
and decryption 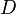 using the key
using the key  ,
,
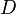 using the key
using the key  ,
, ,
,
whereas 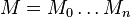 is the message,
is the message,  is the ciphertext and
is the ciphertext and  is the used key.
is the used key.
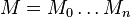 is the message,
is the message,  is the ciphertext and
is the ciphertext and  is the used key.
is the used key.
Thus using the previous example, to encrypt  with key letter
with key letter 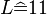 the calculation would result in
the calculation would result in  .
.
 with key letter
with key letter 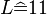 the calculation would result in
the calculation would result in  .
.
Therefore to decrypt 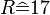 with key letter
with key letter  the calculation would result in
the calculation would result in 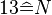 .
.
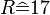 with key letter
with key letter  the calculation would result in
the calculation would result in 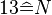 .
.lunes, 20 de agosto de 2012
domingo, 19 de agosto de 2012
martes, 14 de agosto de 2012
[Extra Points] Code Message
El cifrado de Vigenère
El cifrado Vigenère es un cifrado basado en diferentes series de caracteres o letras del cifrado César formando estos caracteres una tabla, llamada tabla de Vigenère, que se usa como clave. El cifrado de Vigenère es un cifrado polialfabético y de sustitución.
El cifrado Vigenère se ha reinventado muchas veces. El método original fue descrito por Giovan Batista Belaso en su libro de 1553 "La cifra del Sig. Giovan Batista Belaso", quien construyó el cifrado basándose en la tabula recta de Trithemius, pero añadió una clave repetida para cambiar cada carácter entre los diferentes alfabetos. Sin embargo, fue incorrectamente atribuido en el siglo XIX a Blaise de Vigenère, a partir de un trabajo realizado en 1583, y por ello aún se le conoce como el "cifrado Vigenère".
Este cifrado es conocido porque es fácil de entender e implementar, además parece irresoluble; esto le hizo valedor del apodo el código indescifrable (le chiffre indéchiffrable, en francés).
El primer cifrado polialfabético fue creado por Leone Battista Alberti hacia 1467 y usaba un disco de metal para cambiar entre los diferentes alfabetos del cifrado. El sistema de Alberti sólo cambiaba entre alfabetos después de muchas palabras, y los cambios se indicaban escribiendo la letra del correspondiente alfabeto en el mensaje cifrado. Más tarde, en 1508, Johannes Trithemius, en su trabajo Poligraphia, inventó la tabula recta, que es básicamente la tabla de Vigenère. Trithemius, sin embargo, sólo proporcionó un progresivo, rígido y predecible sistema de cambio entre alfabetos.
A B C D E F G H I J K L M N Ñ O P Q R S T U V W X Y Z
B C D E F G H I J K L M N Ñ O P Q R S T U V W X Y Z A
C D E F G H I J K L M N Ñ O P Q R S T U V W X Y Z A B
D E F G H I J K L M N Ñ O P Q R S T U V W X Y Z A B C
E F G H I J K L M N Ñ O P Q R S T U V W X Y Z A B C D
F G H I J K L M N Ñ O P Q R S T U V W X Y Z A B C D E
G H I J K L M N Ñ O P Q R S T U V W X Y Z A B C D E F
H I J K L M N Ñ O P Q R S T U V W X Y Z A B C D E F G
I J K L M N Ñ O P Q R S T U V W X Y Z A B C D E F G H
J K L M N Ñ O P Q R S T U V W X Y Z A B C D E F G H I
K L M N Ñ O P Q R S T U V W X Y Z A B C D E F G H I J
L M N Ñ O P Q R S T U V W X Y Z A B C D E F G H I J K
M N Ñ O P Q R S T U V W X Y Z A B C D E F G H I J K L
N Ñ O P Q R S T U V W X Y Z A B C D E F G H I J K L M
Ñ O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
O P Q R S T U V W X Y Z A B C D E F G H I J K L M N Ñ
P Q R S T U V W X Y Z A B C D E F G H I J K L M N Ñ O
Q R S T U V W X Y Z A B C D E F G H I J K L M N Ñ O P
R S T U V W X Y Z A B C D E F G H I J K L M N Ñ O P S
S T U V W X Y Z A B C D E F G H I J K L M N Ñ O P Q R
T U V W X Y Z A B C D E F G H I J K L M N Ñ O P Q R S
U V W X Y Z A B C D E F G H I J K L M N Ñ O P Q R S T
V W X Y Z A B C D E F G H I J K L M N Ñ O P Q R S T U
W X Y Z A B C D E F G H I J K L M N Ñ O P Q R S T U V
X Y Z A B C D E F G H I J K L M N Ñ O P Q R S T U V W
Y Z A B C D E F G H I J K L M N Ñ O P Q R S T U V W X
Z A B C D E F G H I J K L M N Ñ O P Q R S T U V W X Y
El cifrado Vigenère ganó una gran reputación por ser excepcionalmente robusto. Incluso el escritor y matemático Charles Lutwidge Dodgson (Lewis Carroll) dijo que el cifrado Vigenère era irrompible en el artículo "The Alphabet Cipher" para una revista de niños. En 1917, "Scientific American" describió el cifrado Vigenère como imposible de romper. Esta reputación fue mantenida hasta que el método Kasiski (1863) resolvió el cifrado y algunos criptoanalistas habilidosos pudieron romper ocasionalmente el cifrado en el siglo XVI.
El cifrado Vigenère es lo suficientemente simple si se usa con discos de cifrado. Los Estados confederados de América, por ejemplo, utilizaron un disco de cifrado para implementar el cifrado Vigenère durante la Guerra Civil Americana. Los mensajes confederados fueron poco secretos, ya que los miembros de la Unión solían descifrar los mensajes.
Métodos
de cifrado polialfabéticos
Corresponde a la aplicación cíclica de n cifrados monoalfabéticos, (de varios abecedarios desordenados).
- Dada una tabla con un alfabeto por cada letra del abecedario
Método:
Se busca una palabra clave fácil de recordar.
Se escribe la palabra debajo del texto en claro, repitiéndose tantas veces como sea necesario. Cada letra del texto en claro se codifica con el alfabeto de la tabla marcado por la letra inferior, o sea, la letra de la clave que corresponde. -
Se busca una palabra clave fácil de recordar.
Se escribe la palabra debajo del texto en claro, repitiéndose tantas veces como sea necesario. Cada letra del texto en claro se codifica con el alfabeto de la tabla marcado por la letra inferior, o sea, la letra de la clave que corresponde. -
Cifrar:
C = ( M + K ) Mod N)
Descifrar:
M = ( C - K ) Mod N )
N = 26 (letras alfabeto -1 , ya que empezamos de 0)
Mensaje: P A R I S V A U T B I E N U N E M E S S E
Key: L O U P L O U P L O U P L O U P L O U P L
Criptograma:A O L X D J U J E P C T Y I H T X S M H P
Criptoanalisis para el cifrado vigenere usando kasiski
•Ideado en 1863 para romper el cifrado de Vigenere.
•Se basa en que ciertas secuencias de letras aparecen muchas veces en los textos originales, y consecuentemente los textos cifrados con Vigenere tienen las correspondientes secuencias de letras cifradas también muy repetidas.
•Por tanto, la distancia entre las cadenas más repetidas en el texto cifrado debe ser un múltiplo de la longitud de la clave K, y un buen candidato a longitud será el producto de los factores más repetidos en las distancias encontradas.
Texto original: TOBEORNOTTOBE
Clave: NOWNOWNOWNOWN
Texto cifrado: GCXRCNACPGCXR
Pasos del Criptoanálisis:
1. Se buscan los poligramas más repetidos y las distancias desde sus puntos de inicio para cada uno.
2. Se sabe que la longitud de la clave divide a todas esas distancias, por lo que también dividirá a su mcd
3. Se calculan los factores de cada distancia y se descubren los factores más repetidos (candidatos a longitud de clave).
4. Se divide el criptograma en filas según cada longitud candidata (empezando por la mayor) y se compara la distribución de frecuencias de cada columna con la del idioma usado.
Ejemplo :
Si un atacante intercepta el texto cifrado con Vigenere:
ANYVG YSTYN RPLWH RDTKX RNYPV QTGHP HZKFE YUMUS AYWVKZYEZM
EZUDL JKTUL JLKQB JUQVU ECKBN RCTHP KESXM AZOEN SXGOLPGNLE EBMMT
GCSSV MRSEZ MXHLP KJEJH TUPZU EDWKN NNRWA GEEXSLKZUD LJKFI
XHTKP IAZMX FACWC TQIDU WBRRL TTKVN AJWVB REAWT NSEZM OECSS
VMRSL JMLEE BMMTG AYVIY GHPEM YFARW AOAELUPIUA YYMGE EMJQK
SFCGU GYBPJ BPZYP JASNN FSTUS STYVG YS
•Texto descifrado:
If signals are to be displayed in the presence ofan enemy, they must be guarded by ciprés. The ciphers must be capable of frequent changes. The rules by which these changes are made must be simple. Ciphers are undiscoverable in proportion as their changes are frequent and as the messages in each change are brief. From Albert J. Myer’s Manual of Signals
Mas information
http://cryptull.webs.ull.es/TallerCripto/Criptoanalisis.pdf
El Codigo esta en python:
El Codigo esta en python:
Suscribirse a:
Entradas (Atom)